Member-only story
Tier 1 — Hack The Box — Mission: Crocodile
Today, we’re diving into the Hack The Box trial challenge called “Alligator,” where you’ll encounter an FTP server with anonymous access enabled. This vulnerability opens the door to exploring further into the system, allowing us to gather crucial information and eventually gain access to the target web server. This guide will take you through each step, helping you understand how to leverage FTP vulnerabilities in real-world scenarios while building your skills in penetration testing.
- Understanding FTP and Anonymous Access
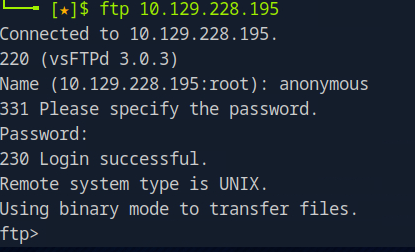
FTP (File Transfer Protocol) is a standard network protocol used to transfer files between clients and servers. While it’s a common service, FTP can sometimes be misconfigured, leading to vulnerabilities that hackers can exploit. One of the most common misconfigurations is anonymous FTP access, which allows users to log in without a username or password. This opens up the server to unauthorized access and can expose sensitive information.
In this challenge, you’ll exploit anonymous FTP access to gain insights into the target machine’s file system. From there, you can gather the information needed to proceed further into the web server.
Task 1
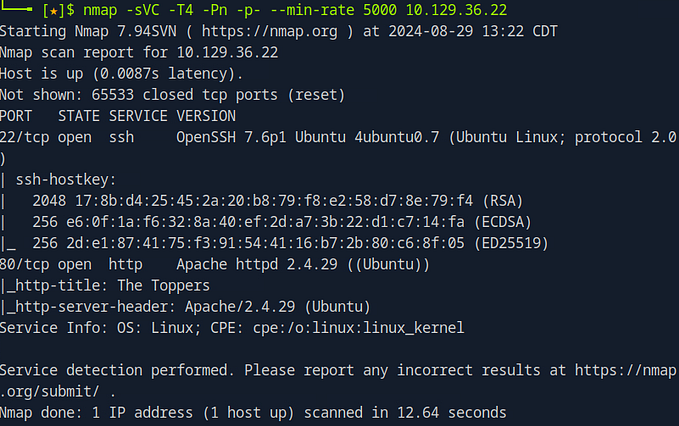
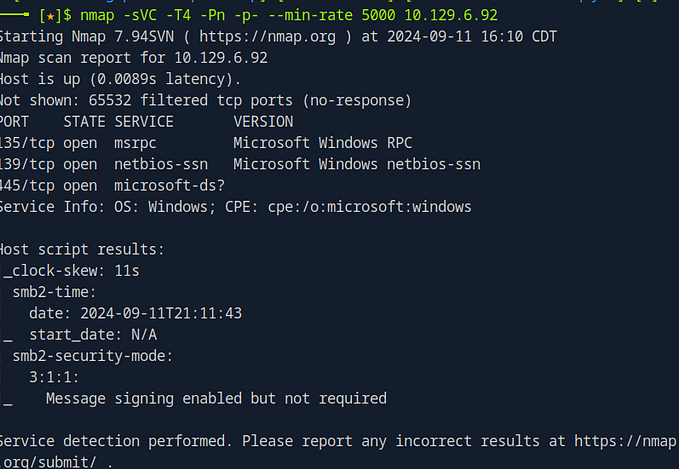
In penetration testing, Nmap is one of the most powerful tools for gathering information about a target machine. One of its useful features is the ability to run default scripts during a scan, which can quickly uncover common vulnerabilities and misconfigurations. In this…