Member-only story
Hack the Box — Tactics
Task 1
Windows is one of the most widely used operating systems globally, especially in corporate environments. Its user-friendly interface makes it the go-to for many organizations, but this simplicity can lead to misconfigurations that attackers may exploit. One common vulnerability stems from improperly configured SMB (Server Message Block) shares, which can open up security loopholes in a corporate network.
In this guide, we’ll explore how to identify such vulnerabilities, focusing on a misconfigured SMB share, using tools like Nmap for network scanning. We will also touch on the importance of understanding the consequences of different attack vectors and making informed decisions when approaching a target.
Running the Nmap Scan
When scanning a target network for vulnerabilities, the first step is to gain as much information as possible without raising alarms. Firewalls on corporate networks will often block standard scanning techniques, making it important to employ stealthier options.
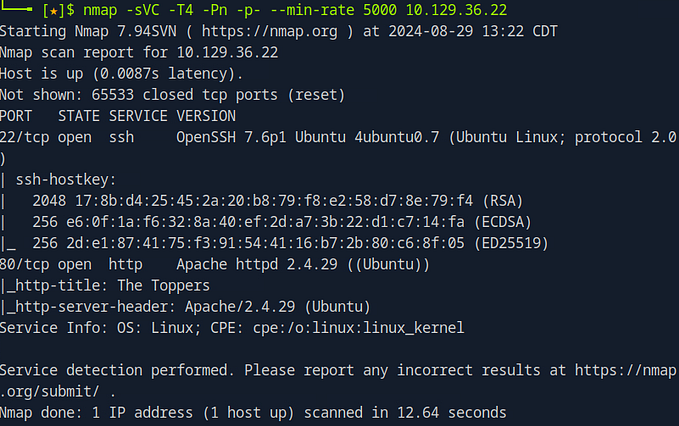
In this scenario, we’ll use Nmap, one of the most popular network scanning tools. Here’s the command we’ll use:
nmap -sVC -T4 -Pn -p- --min-rate 5000 <target ip address>Let’s break down what each switch does:
- -sVC: This combines two switches. The
-sCflag enables Nmap's default scripts, and-sVperforms service version detection. Together, they provide details about the services running…